The Industrial Internet of Things (IIoT) sounds like futuristic—smart factories, automated systems, and seamless integration. The catch is that it’s also a playground for cyber attacks. Whether it’s stealing data, crashing operations, or good old sabotage, hackers are exploiting IIoT vulnerabilities. In this context Digital Forensic Incident Response (DFIR) is a key tool for defending against and investigating these attacks.
Why is IIoT Security Hard?
IIoT connects physical systems (think manufacturing equipment) with digital networks. Great for efficiency, but it also opens the door to cyber-physical attacks. Picture this: malware infects a water treatment plant and tampers with the valves, leading to a toxic spill. Or an oil pipeline operation suffers a ransomware attack that halts operations for a week and leads to fuel panic buying and price surges.
Here’s what makes IIoT so tricky to secure:
- Outdated Systems: Many industrial control systems (ICS) still run on decades-old technology that was never designed to handle today’s threats.
- Complex Architectures: Systems like SCADA integrate sensors, actuators, and communication networks. More connections = more opportunities for hackers.
- Lack of Standards: There’s no one-size-fits-all security model, making it hard to implement consistent defenses.
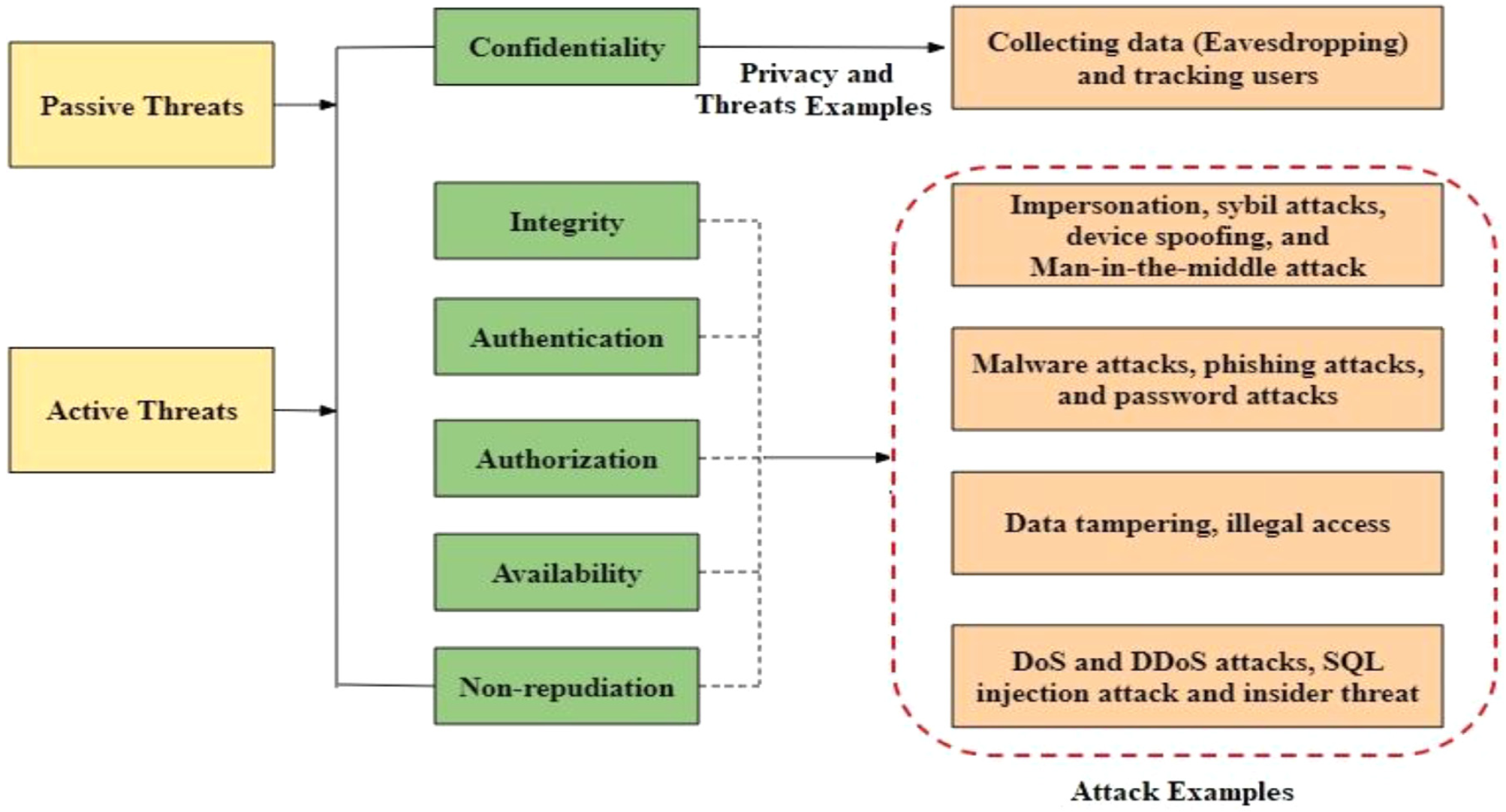
DFIR to the Rescue
Digital Forensic Incident Response (DFIR) isn’t just about investigating crimes after the fact, it’s also about proactively improving security. For IIoT, DFIR helps in:
- Identifying Vulnerabilities: Understanding weak spots before attackers exploit them.
- Analyzing Incidents: Tracing how and why an attack happened.
- Preserving Evidence: Ensuring data integrity for legal or internal reviews.
- Improving Systems: Learning from incidents to strengthen defenses.
DFIR in Action: The SCADA Example
SCADA systems, which control critical infrastructure like power grids and water plants, are prime targets for cyberattacks.
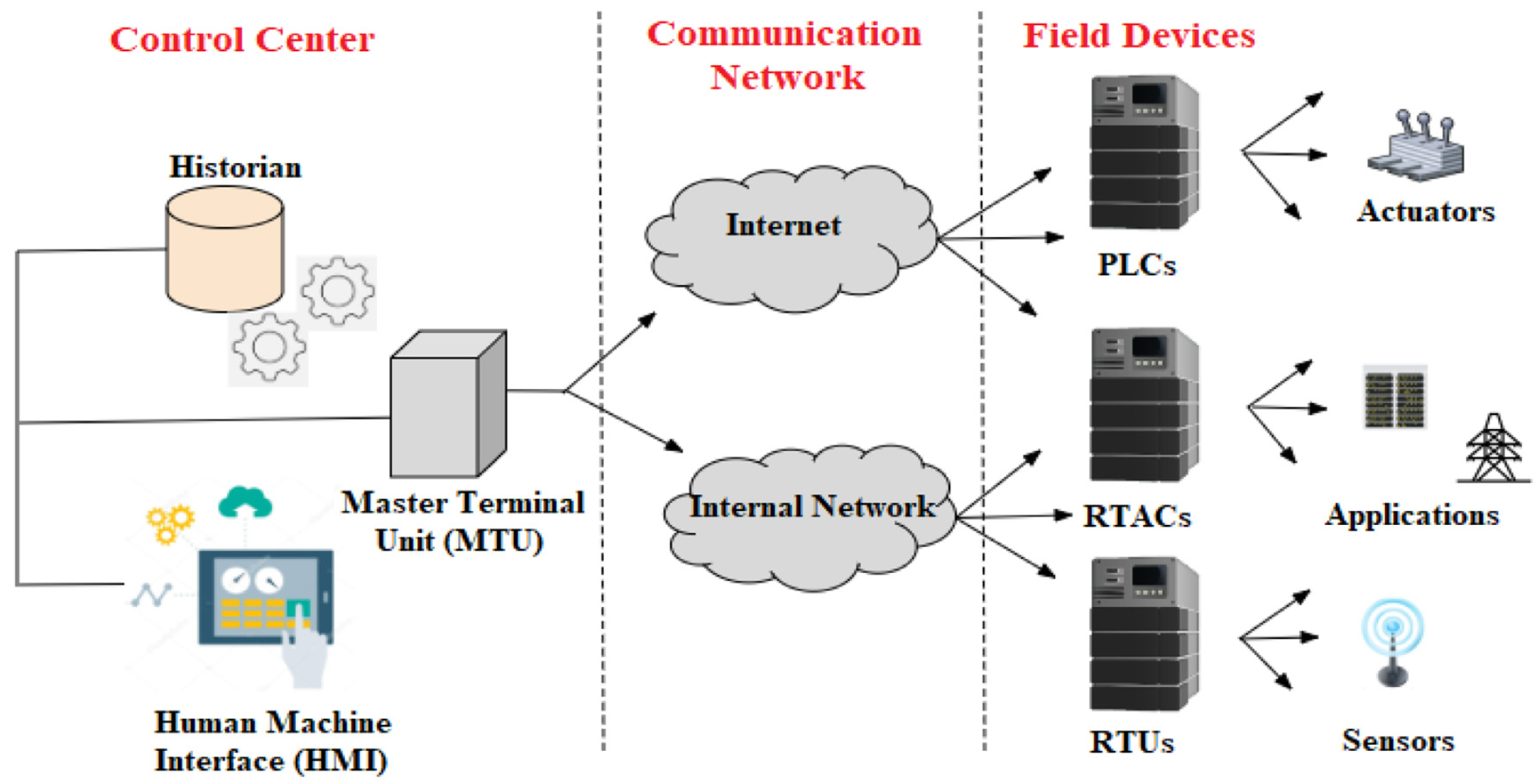
Here’s how a DFIR model works in a SCADA environment:
- Preparation: Map out the system architecture and identify potential attack points.
- Detection: Spot unusual activity, like unauthorized access or malware injections.
- Isolation: Contain the infected areas to prevent further damage.
- Triage: Prioritize evidence collection from the most critical systems.
- Response: Analyze the attack and secure the system.
- Reporting: Create a detailed report to inform future security measures.
Challenges and Gaps
While DFIR is powerful, it’s not a magic bullet. Here are some of the challenges:
- Live Forensics: Collecting data while the system is running without disrupting operations is tough.
- Tool Limitations: Most forensic tools aren’t designed for IIoT’s unique setups.
- Data Integrity: Maintaining the integrity of evidence in constantly evolving environments is tricky.
Why This Matters
DFIR isn’t just about reacting to threats, it’s about staying one step ahead. With cyberattacks on critical infrastructure becoming more common, integrating forensic processes into IIoT systems is no longer optional.
Curious about more? There’s an entire research paper by Pranita Binnar & co. here.