Our smartphones are basically extensions of ourselves at this point. We use them for lots of things, authentication being one of them. And we use our phones a lot for social media (or is it just me?). And, of course, we use our phones to authenticate to social media.
E-BrightPass proposes a malware-proof method for authenticating to social media. So, what’s the big deal?
The Problem With Smartphone Security
Most of us rely on traditional passwords or PINs to log into social media apps. And if we’re feeling extra cautious, we enable two-factor authentication (2FA). But even these methods might not be enough. Assuming a compromised device, malware can record keystrokes, read SMS-based 2FA codes, and even infer PINs by analyzing multiple login attempts.
BrightPass v1: A Clever (But Flawed) Idea
BrightPass was introduced to make smartphone authentication more secure by using screen brightness levels to guide PIN entry. The idea? Make it harder for malware to guess your PIN. But researchers found a flaw. Attackers could record multiple login sessions and piece together the PIN by analyzing patterns in the brightness changes.
So what do you do when you (kind of) fail? You change the name and try again. Enter E-BrightPass, a series of improvements to fix the initial shortcoming while keeping the system user-friendly.
How E-BrightPass Works
E-BrightPass isn’t just a patch job, it’s a full-on upgrade. It introduces three new methods that add layers of complexity to authentication, making it nearly impossible for malware or spyware to crack your PIN.
Method I: The Secret Key Combo
This method mixes your original PIN with a secret key generated from a 2x5 matrix. The final PIN changes every time you log in. For example:
- Original PIN: 1234
- Secret Key: 7582
- Final PIN: 8716
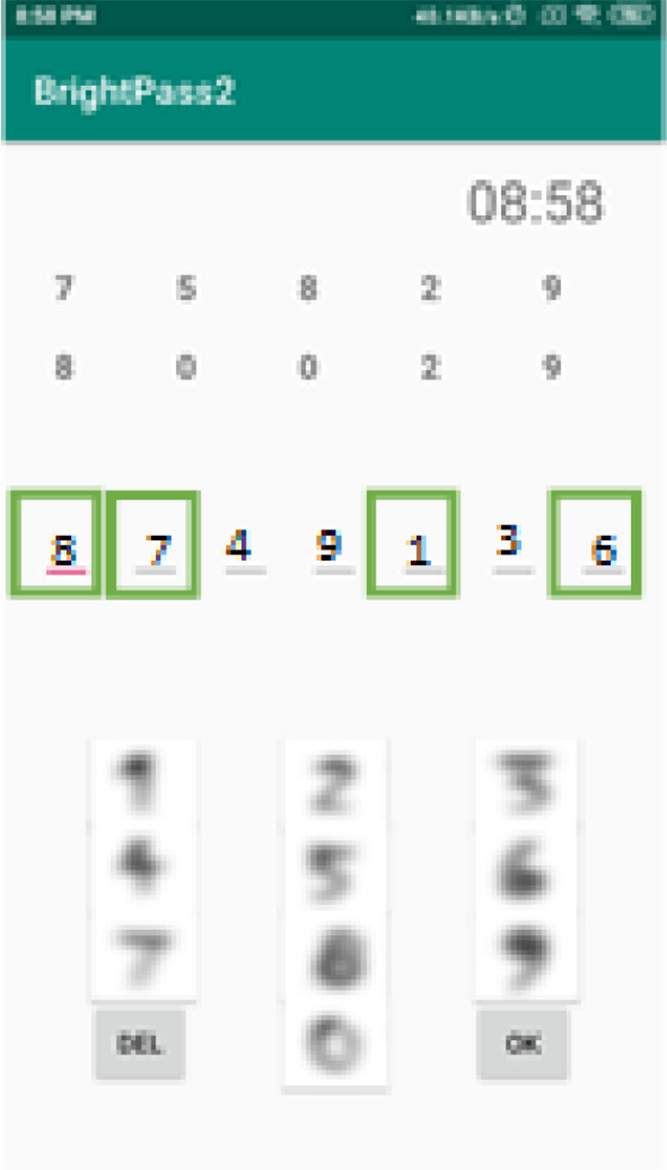
Method II: Graphical Passwords
Think of this as a treasure map for your PIN. A graphical interface displays arrows and numbers, and you follow the directions to create your final PIN. The directions change every session, making it impossible to reuse captured data.
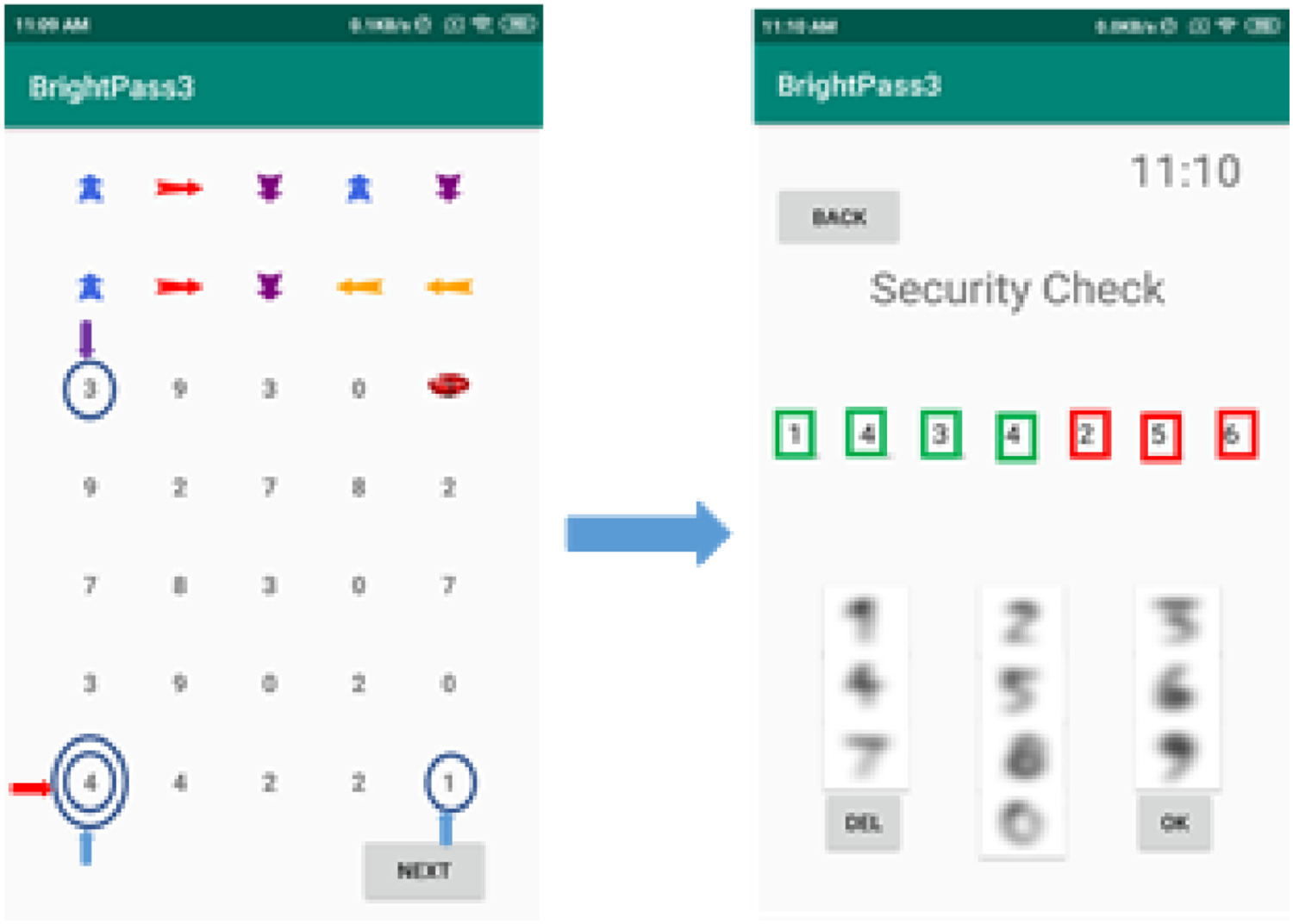
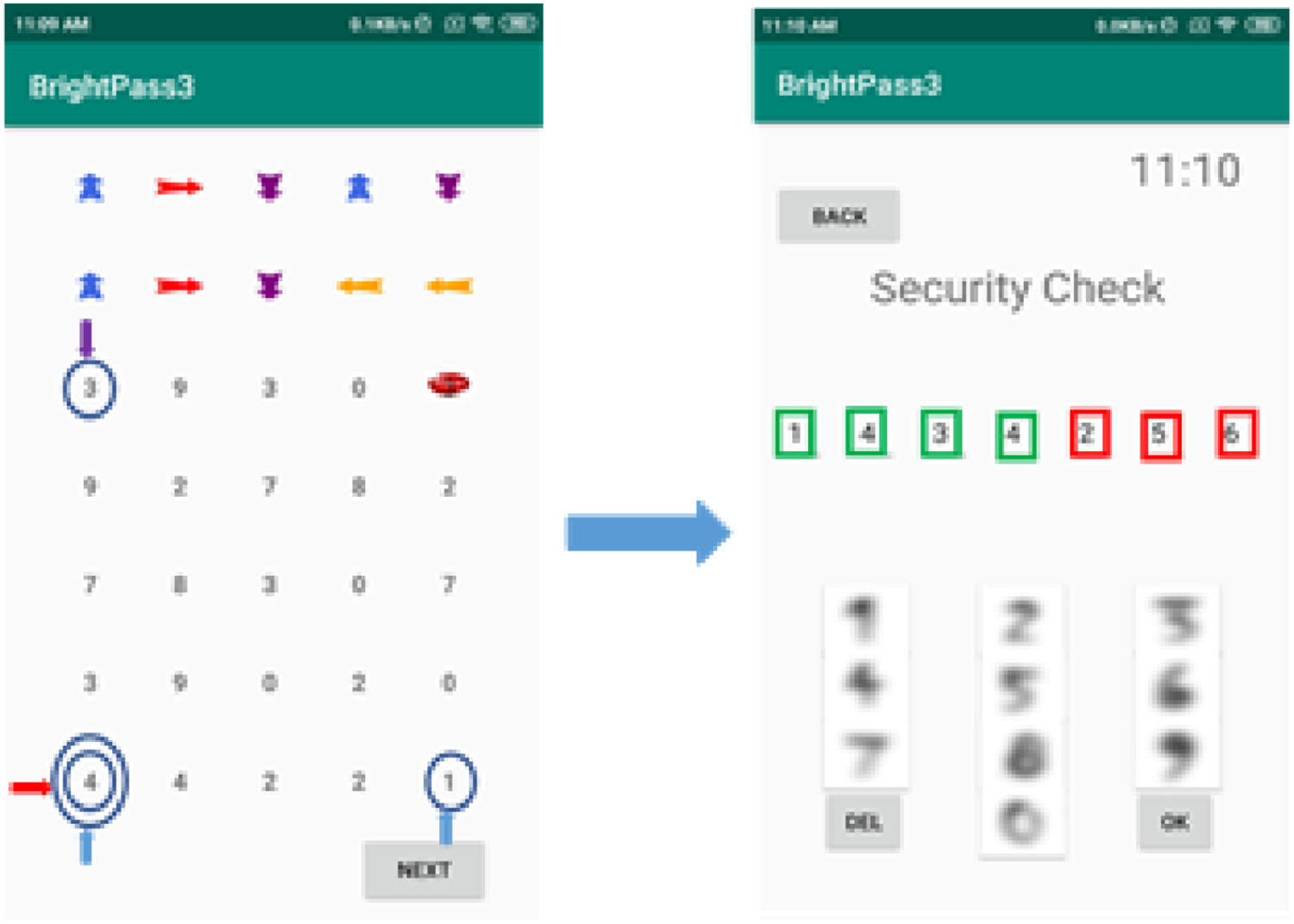
Method III: Brightness Decoy
This one uses screen brightness as both a guide and a decoy. High brightness means you follow the graphical directions; low brightness lets you add random inputs to throw off attackers. Even if malware records your keystrokes, the randomness makes the data useless.
Advantages
These methods make E-BrightPass resistant to:
- Brute force attacks: Randomized PINs make guessing impossible.
- Recording attacks: Even if someone records multiple login sessions, they can’t piece together your PIN.
- Side-channel attacks: Malware can’t exploit brightness or sensor data to crack the system.
In tests, E-BrightPass held up against all common attack types. It does takes a few extra seconds to log in compared to traditional methods, which annoys the hell out of the short attention span people. This is not part of the study, but anectodal evidence from my own adventures. It boils down to the trade-off between security and convenience.
Real-Life Applications
While E-BrightPass was designed with social media in mind, it could work for anything requiring secure logins: banking apps, corporate networks, government systems, etc.
Want to dive into the details? Check out the full research here.