Vehicular Ad Hoc Networks (VANETs) are like the Avengers of the road. Autonomous, connected, and ready to revolutionize transportation. But with great tech comes great vulnerabilities. Distributed Denial-of-Service (DDoS) attacks is one of the most serious threats to VANET Cloud systems. These attacks can clog networks, disrupt communication, and make a smart car, well, not-so-smart.
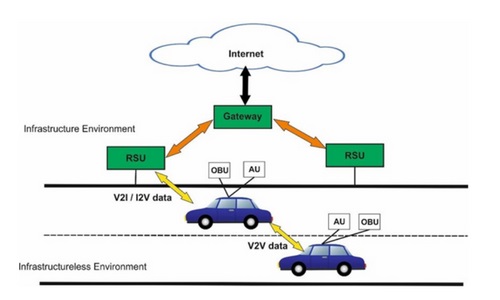
Thankfully, researchers are on it. There are studies out there proposing a machine learning-based framework to detect DDoS attacks in VANET Clouds with a jaw-dropping accuracy of 99.59%.
DDoS Attacks Are a Nightmare
DDoS attacks aren’t new, but in VANET Clouds, they’re extra problematic.
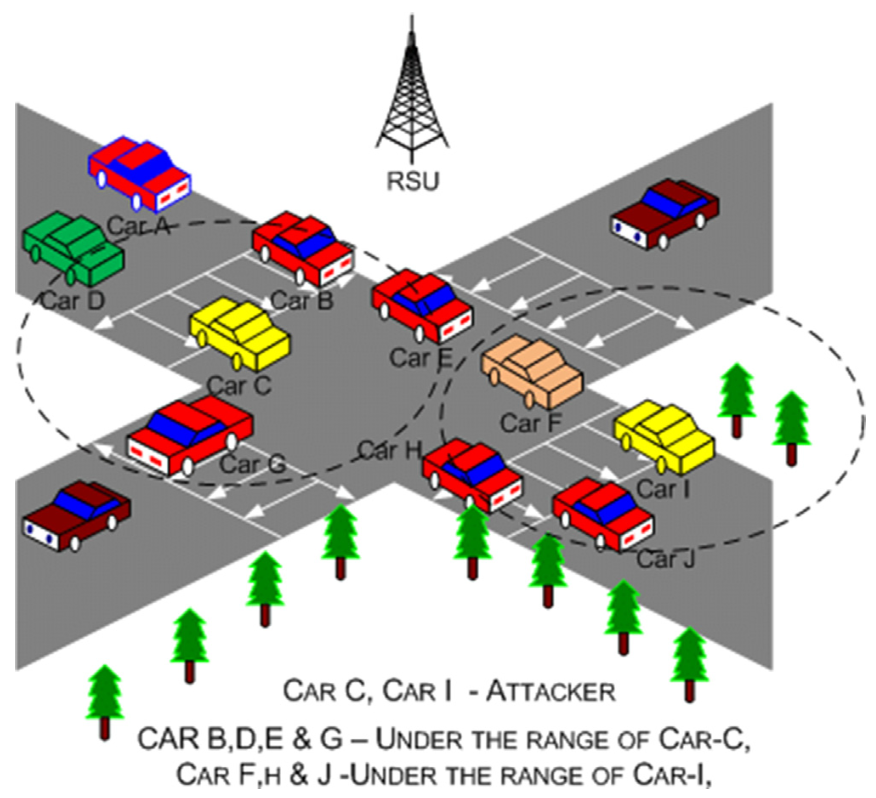
- Dynamic Networks: VANET Clouds involve moving vehicles and decentralized systems. This makes it hard to identify malicious nodes.
- Low Tolerance for Delays: When lives are at stake (think self-driving cars), even small delays in communication can lead to disaster.
- Sophisticated Techniques: Attackers use tricks like IP spoofing and botnets, making traditional defenses ineffective. Traditional defenses which are anyway deployed on traditional infrastructure.
The Two-Phase Solution
Researchers have proposed a two-phase methodology to tackle this.
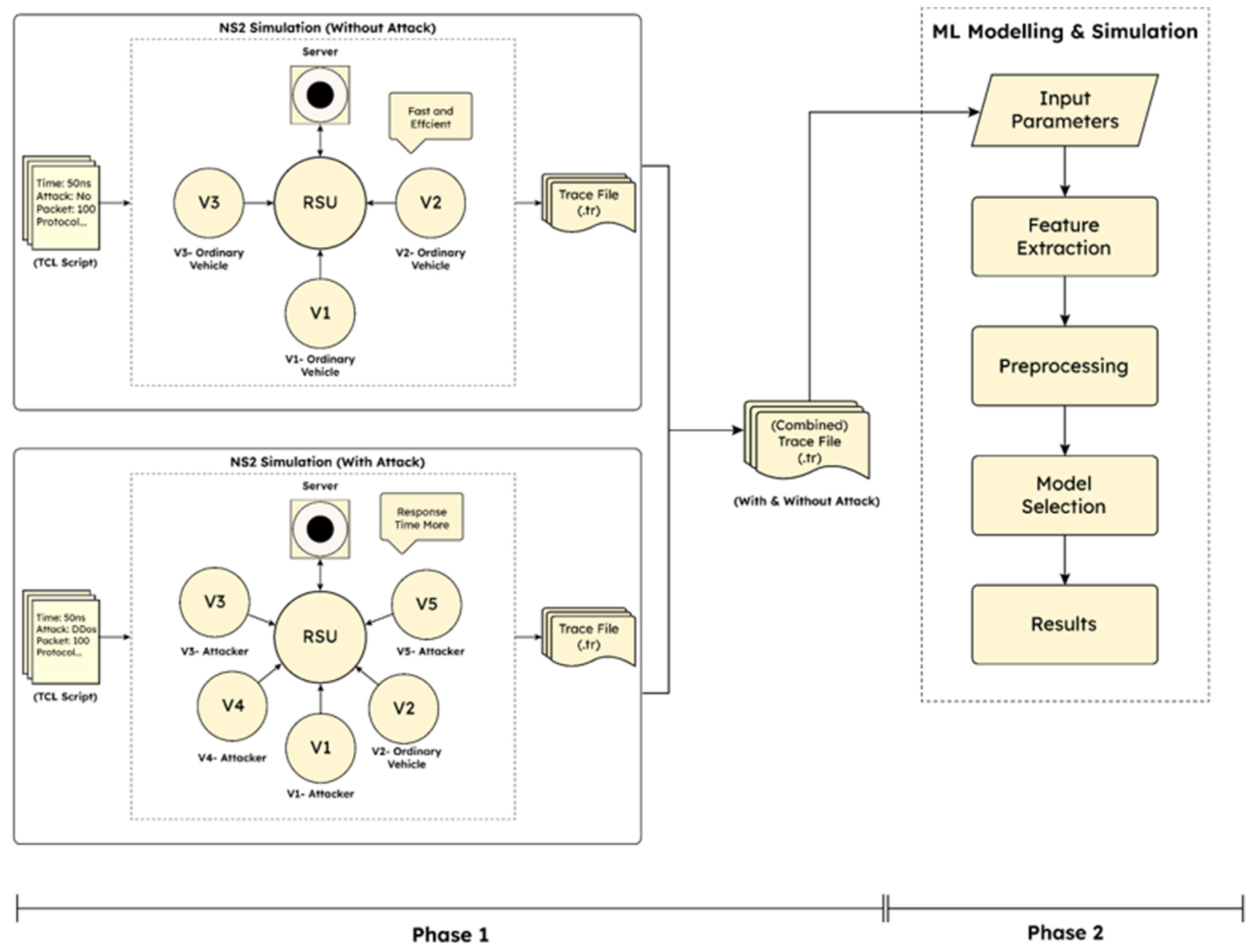
Phase 1: NS2 Simulation
This phase uses the NS2 simulator to model DDoS attacks in VANET Clouds. It works something like this:
- Create Two Scenarios: One normal (no attacks) and one with attackers disrupting communication.
- Simulate Packet Flow: Track how packets move between vehicles and road-side units (RSUs).
- Measure the Damage: Calculate metrics like Packet Delivery Ratio (PDR) and energy consumption to assess the impact of the attacks.
Phase 2: Machine Learning Models
The data from Phase 1 is fed into various machine learning models to classify network activity as either “normal” or “DDoS attack.” Models tested include:
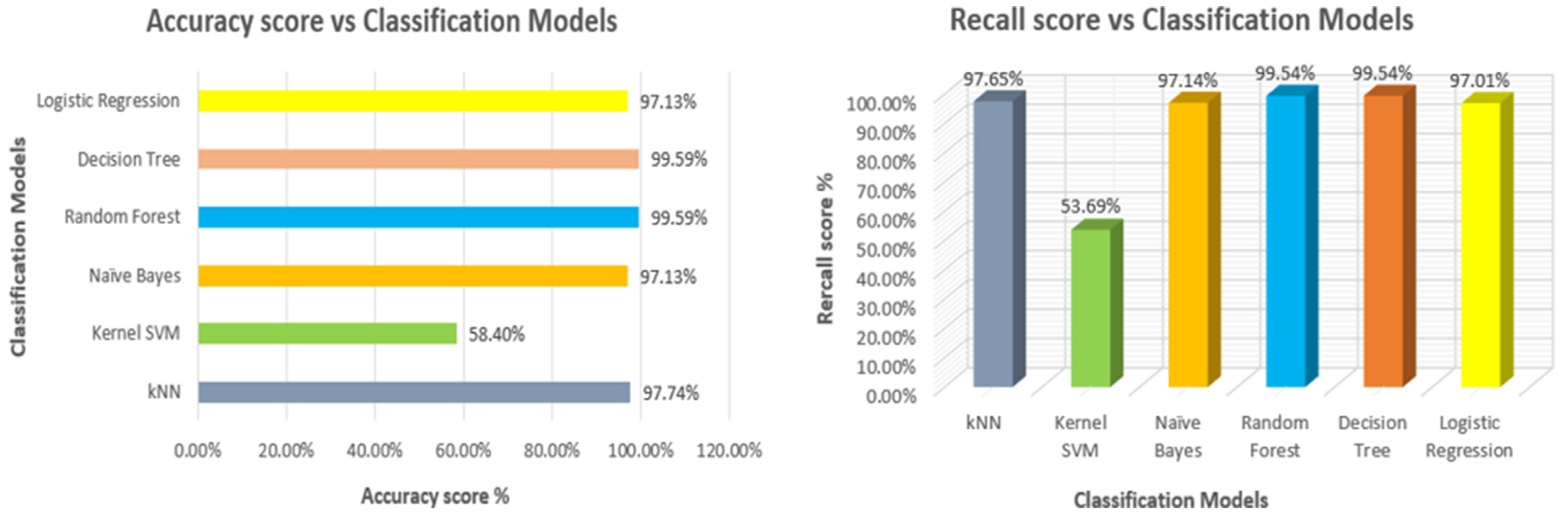
- Random Forest (best performer)
- Decision Tree (equally good)
- Logistic Regression, Naive Bayes, and K-Nearest Neighbor (solid but not the best)
- Kernel SVM (let’s just say it needs some work)
The Random Forest and Decision Tree models achieved near-perfect accuracy, making them the go-to options.
Fuzzification Is The Secret Sauce
To handle fuzzy data (like borderline cases), a fuzzification algorithm is the way to go. Think of it as a way to handle the gray areas where data isn’t clearly “normal” or “malicious.” By assigning membership values, the system can make more precise decisions.
Results That Speak for Themselves
- Random Forest and Decision Tree models are nailing it, with accuracy, precision, recall, and F1 scores all hitting 99.59%.
- Metrics like PDR showed clear differences between normal and attack scenarios, making them reliable indicators for detection.
- Energy consumption trends were also useful for spotting anomalies.
Takeaway
DDoS attacks are a serious threat to VANET Clouds, but machine learning is proving to be a powerful defense.
Want to geek out on the details? Check out one of the studies here.